Introduction
The rapid growth of the Internet of Things (IoT) has transformed the way we live and work. From smart homes and wearable devices to industrial IoT systems and smart cities, billions of devices are now connected, generating massive amounts of data every second. However, this connectivity comes with a significant risk: IoT security challenges. Weak security can expose devices and networks to cyberattacks, data breaches, and operational disruptions.
IoT security solutions are essential to safeguard connected devices, ensure data integrity, and protect privacy. These solutions encompass device authentication, encryption, network security, cloud security, AI-powered monitoring, and regulatory compliance. As IoT adoption grows, the demand for comprehensive security solutions is becoming a top priority for businesses, governments, and consumers alike.
The complexity of IoT networks introduces unique challenges: limited computing resources on devices, diverse communication protocols, inconsistent security standards, and continuous device deployment. Addressing these issues requires a layered approach, combining hardware-based protections, software security measures, and ongoing monitoring.http://futuretechfrontier.com
In this article, we will explore everything you need to know about IoT security solutions—from the threat landscape and key components to advanced technologies, best practices, real-world case studies, and future trends. By the end, readers will have a clear understanding of how to protect IoT ecosystems effectively and future-proof their connected devices.
Understanding IoT Security Challenges
The proliferation of IoT devices has brought tremendous convenience, automation, and data-driven insights. However, the rapid growth of connected devices also introduces complex security challenges. Without robust IoT security solutions, these devices can become entry points for cyberattacks, leading to data breaches, operational disruption, and financial losses. Understanding these challenges is the first step in building a secure IoT ecosystem.
Common IoT Security Threats
IoT devices face a wide range of security threats due to their connected nature and limited security features. Some of the most common threats include:
- Malware and ransomware attacks: IoT devices can be infected with malicious software, turning them into bots for attacks or locking data until a ransom is paid.
- Distributed Denial of Service (DDoS) attacks: IoT botnets, like the infamous Mirai botnet, can overwhelm networks, causing widespread service disruptions.
- Data breaches and unauthorized access: Inadequate authentication and weak security measures allow attackers to steal sensitive information from smart devices and industrial systems.
- Physical tampering: Many IoT devices are deployed in public or uncontrolled environments, making them vulnerable to direct physical attacks.
Fact: A 2024 report from Cybersecurity Ventures predicts that IoT attacks will reach 50 billion devices annually by 2027, highlighting the urgent need for effective IoT security solutions.
Vulnerabilities in IoT Devices
IoT devices are often resource-constrained, meaning they have limited processing power, memory, and energy. This limitation leads to common vulnerabilities:
- Weak/default passwords and authentication: Many devices are shipped with default credentials that users fail to change, making them easy targets.
- Insecure communication protocols: Unencrypted protocols like HTTP or MQTT can expose sensitive data to interception.
- Lack of firmware updates: Devices without secure update mechanisms remain vulnerable to known exploits.
- Inconsistent security standards: Manufacturers may implement different security measures, leading to gaps in protection across networks.
Risks of Inadequate IoT Security
Failing to implement proper IoT security solutions can have serious consequences:
- Privacy violations: Personal and sensitive data, including location and health information, can be exposed.
- Financial losses: Cyberattacks can result in operational downtime, legal penalties, and loss of customer trust.
- Reputational damage: Organizations suffering from IoT breaches risk losing credibility and customer confidence.
- Critical infrastructure compromise: Industrial IoT, healthcare devices, and smart city systems can be disrupted, causing safety hazards and widespread impact.
Example: In 2021, a breach in a hospital’s connected medical devices allowed attackers to access patient data and disrupt operations, emphasizing the need for robust IoT security strategies.
Key Components of IoT Security Solutions
Implementing effective IoT security solutions requires a multi-layered approach that protects devices, networks, and data across the entire ecosystem. Modern IoT security strategies rely on a combination of device-level protections, secure communication protocols, network security, cloud safeguards, and robust software management. Understanding these components is essential to building a resilient and trustworthy IoT infrastructure.
Device Authentication and Identity Management
One of the foundational pillars of IoT security solutions is ensuring that only authorized devices can connect to the network. Weak or missing authentication allows attackers to impersonate devices and gain access to sensitive systems.
Key strategies:
- Digital certificates and cryptographic keys for secure device identity
- Mutual authentication protocols to verify both device and network
- Biometric or hardware-based identity solutions for high-security IoT devices
Example: Industrial IoT systems often implement hardware security modules (HSMs) to manage device identities and cryptographic keys securely.
Encryption and Secure Communication
IoT devices transmit vast amounts of sensitive data over networks, making encryption a critical security layer. Encryption ensures that even if attackers intercept data, it remains unreadable.
Key techniques:
- Data encryption in transit and at rest using AES, RSA, or ECC algorithms
- Secure protocols like TLS, HTTPS, and DTLS for communication
- Lightweight encryption tailored for resource-constrained IoT devices
Fact: A study by IoT Analytics (2023) found that over 60% of IoT devices in use still rely on unencrypted communication, highlighting the urgent need for encryption-focused IoT security solutions.
Firmware and Software Security
Many IoT breaches occur due to outdated firmware or insecure software. Ensuring devices run secure, up-to-date software is a critical part of IoT protection.
Best practices include:
- Secure boot mechanisms that verify firmware integrity at startup
- Code signing to prevent unauthorized firmware from running
- Regular software updates and patch management to fix vulnerabilities
Example: Smart home hubs and industrial IoT gateways often implement over-the-air (OTA) updates, allowing remote patching while maintaining security.
Network Security Solutions
IoT networks must be segmented and monitored to prevent threats from spreading across systems. Network-level protections are a core component of IoT security solutions.
Key elements:
- Firewalls and intrusion detection/prevention systems (IDS/IPS) for monitoring traffic
- Segmentation of IoT networks to isolate devices from critical infrastructure
- Anomaly detection and real-time monitoring to identify unusual activity
Fact: The Mirai botnet attack (2016) exploited unsecured IoT devices to launch a massive DDoS attack, demonstrating the importance of robust network security in IoT ecosystems.
Cloud and Platform Security
Many IoT systems rely on cloud platforms for data storage, analysis, and device management. Securing the cloud layer is essential for end-to-end IoT protection.
Strategies include:
- Secure IoT cloud platforms with strong access controls
- Data isolation and multi-tenant security for shared cloud environments
- Endpoint-to-cloud encryption and continuous monitoring
Example: AWS IoT and Microsoft Azure IoT provide built-in security features such as certificate-based authentication, role-based access, and automatic encryption to safeguard IoT deployments.
Advanced IoT Security Solutions and Technologies
As IoT networks grow more complex, traditional security measures are no longer sufficient. Advanced IoT security solutions leverage cutting-edge technologies such as artificial intelligence (AI), blockchain, zero trust models, and edge/fog computing to protect devices and data from increasingly sophisticated threats. These technologies enable real-time threat detection, automated response, and secure decentralization in connected systems.
Artificial Intelligence and Machine Learning for IoT Security
AI and machine learning (ML) are transforming IoT security by enabling behavioral monitoring, anomaly detection, and predictive threat management. Unlike static security rules, AI can adapt to changing attack patterns and large-scale IoT networks.
Applications include:
- Behavior-based anomaly detection: Identifies unusual device activity that may indicate compromise
- Predictive threat intelligence: Anticipates potential attacks before they happen
- Automated response: AI can quarantine compromised devices or adjust network rules in real-time
Case Study: NVIDIA’s AI-powered monitoring tools analyze IoT traffic in smart factories, detecting and isolating unusual behavior within milliseconds, reducing false positives by over 40%.
Blockchain-Based Security Solutions
Blockchain provides a decentralized and tamper-proof framework for IoT security, addressing challenges like device authentication, data integrity, and secure transactions.
Advantages of blockchain in IoT security:
- Decentralized authentication: Eliminates single points of failure in device identity management
- Immutable data records: Ensures that IoT-generated data cannot be altered or falsified
- Smart contracts: Automate security policies, compliance checks, and device interactions
Use Cases:
- Supply chain IoT: Tracking products and verifying authenticity
- Smart homes: Secure peer-to-peer device communication
- Healthcare IoT: Ensuring integrity of patient data in connected medical devices
Zero Trust Security Models for IoT
The zero trust model assumes that no device, user, or network is inherently trustworthy. In IoT ecosystems, this approach ensures continuous verification, limiting the spread of attacks.
Key principles:
- Continuous authentication: Devices and users are verified before every transaction
- Least privilege access: Devices access only the resources they need
- Micro-segmentation: Reduces lateral movement in case of a breach
Impact: Organizations adopting zero trust in industrial IoT networks have reported a 60% reduction in unauthorized access incidents, demonstrating its effectiveness for complex IoT ecosystems.
Edge and Fog Security
Edge and fog computing bring computation and security closer to IoT devices, reducing latency and dependency on centralized servers. Security at the edge ensures real-time threat detection and data protection.
Benefits include:
- Local data encryption and processing to reduce exposure during transmission
- Real-time anomaly detection for autonomous vehicles, smart factories, and medical devices
- Reduced bandwidth and cloud dependency, enhancing performance and security
Example: Smart city traffic sensors use fog computing nodes to detect anomalies locally before sending only aggregated, encrypted data to the central cloud, minimizing exposure to attacks.
Best Practices for Implementing IoT Security Solutions
Implementing robust IoT security solutions requires more than technology—it demands a comprehensive strategy that encompasses policies, lifecycle management, employee awareness, and continuous monitoring. By following best practices, organizations can minimize vulnerabilities, protect data, and ensure the long-term reliability of IoT networks.
Establishing Security Policies and Governance
A strong foundation begins with clear security policies and governance frameworks. These policies define responsibilities, set security standards, and ensure compliance across all devices and networks.
Best practices include:
- Defining an IoT security framework aligned with organizational goals
- Complying with global standards such as ISO/IEC 27001, NIST IoT guidelines, and GDPR
- Regularly updating policies to reflect emerging threats and technology changes
Impact: Organizations with strong governance structures experience 30–40% fewer security incidents, as policies guide consistent security practices across all IoT deployments.
Device Lifecycle Management
IoT security is not just about initial deployment—it spans the entire device lifecycle, from provisioning to decommissioning.
Key steps include:
- Secure provisioning: Ensuring devices are configured securely before deployment
- Ongoing maintenance: Regular firmware updates, patches, and integrity checks
- Decommissioning: Properly wiping data and disabling devices when retired
Example: Large industrial IoT networks implement automated firmware updates and audit logs to ensure all devices remain compliant and secure throughout their lifecycle.
Employee Awareness and Training
Human error is a significant contributor to IoT security breaches. Educating employees and stakeholders is critical.
Best practices include:
- Training staff on password hygiene, secure device usage, and firmware updates
- Conducting regular workshops on IoT security threats and mitigation strategies
- Creating a culture of security awareness within the organization
Fact: A study by Ponemon Institute (2023) found that organizations with IoT-focused employee training reduced insider-related breaches by over 50%.
Continuous Monitoring and Incident Response
Security is not static. Continuous monitoring and an effective incident response plan are essential for detecting threats, mitigating risks, and minimizing downtime.
Best practices include:
- Real-time monitoring of devices and network traffic for anomalies
- Automated alerts and response mechanisms for potential security breaches
- Regular penetration testing, audits, and vulnerability assessments
- Documented incident response plans to handle breaches efficiently
Example: Smart city infrastructure uses centralized dashboards and AI analytics to detect abnormal traffic patterns, isolate compromised sensors, and prevent cascading failures.
Future Trends in IoT Security Solutions
As IoT adoption continues to accelerate, IoT security solutions must evolve to address emerging threats and leverage cutting-edge technologies. The future of IoT security focuses on autonomous defenses, decentralized trust, regulatory alignment, and preparation for quantum computing threats. These trends will shape the way connected devices are protected in the coming years.
AI-Powered Autonomous Security Systems
Artificial intelligence (AI) and machine learning (ML) will increasingly drive autonomous IoT security. These systems can detect threats in real-time, predict attacks before they occur, and automatically respond without human intervention.
Key trends include:
- Self-healing networks: Systems that isolate or quarantine compromised devices automatically
- Predictive analytics: Anticipating new vulnerabilities and mitigating them proactively
- Automated policy adjustments: AI dynamically adjusts device permissions and network access
Example: Autonomous IoT security platforms are already being deployed in smart factories, where AI detects anomalies in device behavior and mitigates potential threats within seconds, preventing costly downtime.
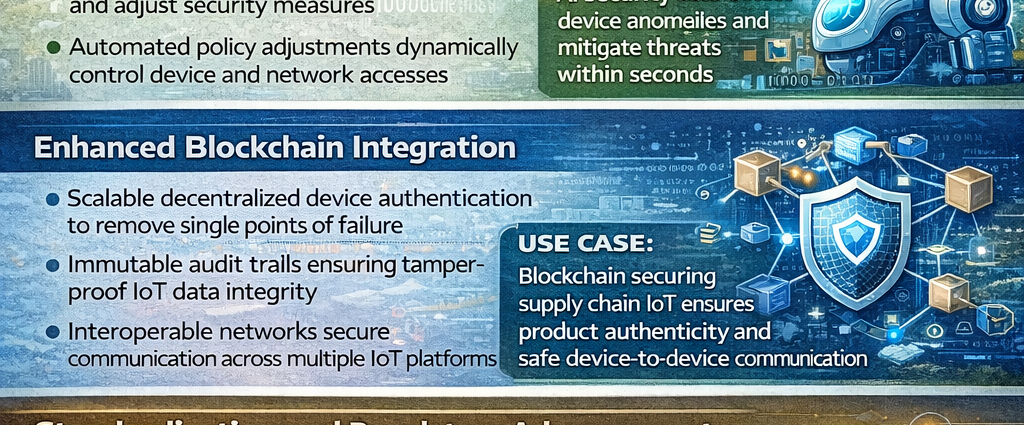
Enhanced Blockchain Integration
Blockchain technology offers a secure, decentralized framework for managing device identity, data integrity, and secure transactions across IoT ecosystems.
Future applications include:
- Scalable device authentication: Eliminating central points of failure in IoT networks
- Immutable audit trails: Ensuring data generated by IoT devices cannot be tampered with
- Interoperable networks: Facilitating secure communication across multiple IoT vendors and platforms
Use Case: Blockchain-based solutions are being explored for supply chain IoT, ensuring product authenticity and secure device-to-device communication.
Standardization and Regulatory Advancements
As IoT devices proliferate, global standards and regulations will play a key role in improving security across industries.
Emerging trends include:
- Adoption of standardized security frameworks such as ETSI EN 303 645 for consumer IoT
- Government regulations requiring minimum security standards for connected devices
- Industry-driven initiatives for interoperable and secure IoT networks
Impact: Standardization will reduce fragmentation in security practices, making IoT networks more resilient and easier to manage.
Quantum-Resistant IoT Security
Quantum computing poses a future threat to traditional encryption methods. To safeguard IoT devices, security solutions are beginning to adopt quantum-resistant cryptography.
Key considerations:
- Developing encryption algorithms that withstand quantum attacks
- Upgrading device communication protocols to be quantum-secure
- Future-proofing IoT ecosystems for post-quantum security challenges
Fact: The National Institute of Standards and Technology (NIST) is actively working on post-quantum cryptography standards, ensuring IoT devices remain secure in the era of quantum computing.



Comments are closed, but trackbacks and pingbacks are open.